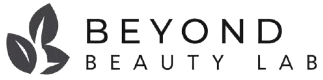Why IP2 Network Matters for Your Digital Wellness
The IP2 network is a decentralized, privacy-first network that puts data control back in users’ hands. Unlike traditional internet protocols, it enables direct, encrypted communication without middlemen or centralized servers.
Key IP2 Network Features:
- Decentralized architecture – No single point of failure
- Built-in privacy – End-to-end encryption and IP masking
- Censorship resistance – Unrestricted access to information
- Improved security – AI-driven threat detection and prevention
- Performance optimization – Intelligent routing and low latency
Just as you carefully choose clean, sustainable beauty products for your skin’s health, your digital wellness deserves the same thoughtful approach. The IP2 network represents a shift toward taking control of your online presence – much like choosing transparency in skincare ingredients.
While traditional networks route your data through corporate servers that can monitor, store, or restrict your activity, the IP2 network creates direct connections between devices. This peer-to-peer approach means your digital footprint stays under your control.
It’s worth noting that “IP2” can also refer to a streaming community connected to Ice Poseidon and the #RV6 phenomenon. However, this guide focuses on the network technology that prioritizes privacy and decentralization.
The IP2 network uses robust encryption to keep your data confidential during transmission. It routes information through the most efficient paths, bypassing geographical restrictions and potential surveillance. With a node-based architecture where every connected device becomes part of the network, it offers true decentralization.
ip2 network vocab to learn:
What Is the IP2 Network? A Deep Dive into the Technology
Think of the IP2 network as a wellness-conscious approach to digital communication. Like choosing organic ingredients for your health, it prioritizes your digital wellbeing by putting privacy and security first.
The IP2 network operates on a peer-to-peer (P2P) architecture. Instead of your data traveling through big corporate servers that can monitor you, it creates direct connections between devices. Every computer, phone, or device that joins becomes a node in this interconnected web.
Traditional networks are like a monitored telephone operator; the IP2 network is a direct, private line. Your data travels encrypted and secure through a mesh of connected devices.
This decentralized approach means no single company controls the flow of information. It’s genuinely censorship-resistant because there’s no central switch to cut you off. The network becomes stronger as more people join – it’s truly powered by its community.

What makes this particularly exciting is how it promotes freedom of information. Because no single entity controls the network, it’s much harder for anyone to block websites or restrict communications. You maintain complete data control over your digital footprint.
To learn more about the fundamental concepts, explore our guide on What is IP2 Network?.
How the ip2 network Differs from IPv4 and IPv6
Understanding how the IP2 network differs from traditional internet protocols is like comparing a farmer’s market to a big box store. Both get you what you need, but the philosophy is completely different.
Traditional protocols like IPv4 and IPv6 route your data through centralized servers and internet service providers. Your message might travel hundreds of miles through corporate data centers, each potentially logging your activity. It’s efficient, but not private.
The IP2 network works as an overlay network – a secure, private layer on top of the existing internet. While it uses the physical internet infrastructure, it creates direct communication pathways that bypass traditional routing.
Instead of predetermined paths controlled by big corporations, the IP2 network uses dynamic routing mechanisms. Your data finds the most efficient route in real-time, adapting to network conditions and avoiding bottlenecks. There are truly no middlemen monitoring or restricting your communications.
This approach offers genuine privacy by design. While IPv4 and IPv6 have served us well, they were built in an era when privacy concerns weren’t as pressing as they are today.
The “Other” IP2: Clarifying the Ice Poseidon Connection
We need to clarify a point of confusion. The term “IP2” is also associated with the streaming community of Ice Poseidon and events like #RV6. This community, known for its sometimes controversial content and cultural phenomenon status in certain internet circles, is entirely separate from the network technology we’re discussing.
Our focus is exclusively on the network technology that prioritizes your digital wellness and security. This aligns with our mission at Beyond Beauty Lab to help you make informed choices for your digital health, just as we do with beauty and wellness practices. The IP2 network we’re exploring represents a thoughtful, privacy-conscious approach to online communication.
Core Features and Benefits of a Decentralized Web
Protecting your digital life requires the same care as choosing a skincare routine. We should be as mindful of our digital tools as we are of product ingredients. The decentralized web, led by technologies like the IP2 network, offers essential benefits for our digital wellness.

Think of traditional internet infrastructure like a beauty product with hidden ingredients – you never know what’s happening behind the scenes. The IP2 network takes a different approach, much like clean beauty brands that prioritize transparency. It’s built on principles that improve your privacy by design, improve security, and boost the performance of your online activities.
The beauty of true decentralization lies in its resilience. Unlike centralized systems with single points of failure, the IP2 network spreads its strength across countless nodes. This creates a robust foundation that’s incredibly hard to disrupt.
This approach puts control back in your hands. There’s no central authority storing your data or monitoring your every move. Instead, you get built-in encryption, anonymity protection, and unrestricted access to information – all while enjoying better performance than traditional networks.
For a deeper dive into these advantages, check out our comprehensive overview of IP2 Network Features and Benefits.
Improved Privacy and Security
Protecting online privacy is like protecting skin from environmental damage – it requires the right tools and consistent care. The IP2 network acts like a digital sunscreen, offering comprehensive, behind-the-scenes protection.
The foundation of this protection is robust encryption. Every piece of data you send gets wrapped in advanced encryption techniques, including SSL/TLS protocols. Think of it as sealing your personal letters in an unbreakable envelope.
But the protection doesn’t stop there. The network uses sophisticated IP masking techniques that hide your real location and identity. It’s like wearing a privacy mask that makes you invisible to trackers. This anonymity feature means your online activities can’t be easily traced back to you.
What really sets the IP2 network apart is its AI-driven threat prevention system. This intelligent layer constantly monitors for suspicious activity and works proactively to stop cyber attacks before they reach you, acting like a personal security guard who never sleeps.
Perhaps most importantly, there’s no central data storage. Traditional networks store your information in massive databases that are tempting targets for hackers. The IP2 network eliminates this risk, as there’s no central vault of user data to breach.
To understand the technicalities of how it keeps us safe, read our article on Understanding IP2 Network Security.
Performance and Scalability
You might think security compromises performance, but the IP2 network often delivers better speed than traditional networks, similar to how high-quality skincare ingredients are more effective.
The secret lies in AI-based intelligent routing. Instead of sending your data along predetermined paths that might be congested, the network’s AI constantly analyzes conditions and finds the fastest routes. This reduces delays and ensures your online experience stays smooth.
This translates to noticeable improvements in Quality of Service (QoS). Whether you’re streaming videos, joining calls, or sharing files, the IP2 network prioritizes important traffic to minimize buffering and maximize clarity. You get low latency for real-time activities and high bandwidth for data-heavy tasks.
The scalability is equally impressive. As more people join, the network gets stronger – each new device becomes part of the infrastructure. This means the IP2 network can handle growth from individual users to large organizations.
The system even includes backward compatibility, so it works seamlessly with existing IPv4 and IPv6 systems. You don’t need to discard your current setup to enjoy the benefits of this next-generation technology.
IP2 Network vs. Alternative Privacy Tools
When you’re choosing the right privacy tool for your digital wellness routine, it’s a bit like selecting the perfect skincare regimen – you want something that balances effectiveness with ease of use. Most of us have heard of VPNs and Tor, but how does the IP2 network stack up against these popular alternatives?
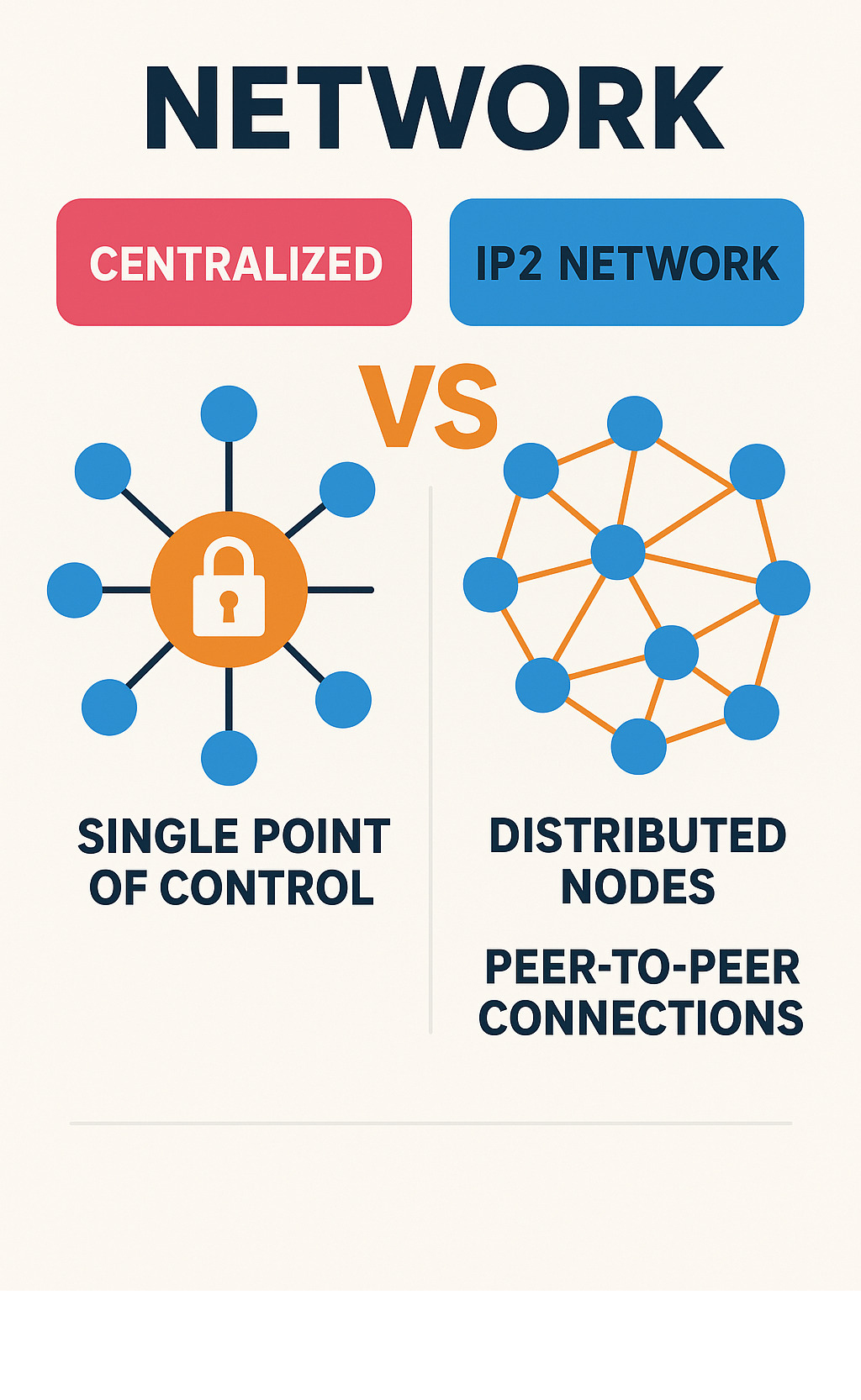
Think of VPNs as your reliable daily moisturizer – they’re straightforward, widely trusted, and get the job done. VPNs create a secure tunnel between your device and their server, encrypting your data and masking your location. They’re incredibly user-friendly, with simple apps that work with just one click. The main catch? You’re essentially trusting a single company with all your data. Just like trusting one brand for all your skincare needs, this centralized approach has its limitations.
Tor is more like a complex, multi-step skincare routine that delivers incredible results but requires patience and dedication. It routes your internet traffic through multiple volunteer-operated relays, encrypting it at each step like layers of an onion. This provides exceptional anonymity and censorship resistance. However, all those layers come at a cost – browsing can be quite slow, and the setup isn’t always beginner-friendly.
The IP2 network finds a sweet spot between these approaches. Unlike VPNs, it doesn’t rely on centralized servers that could become single points of failure. And unlike Tor, it uses AI-based intelligent routing to maintain better performance while still providing robust privacy protection.
| Feature | IP2 Network | VPN | Tor |
|---|---|---|---|
| Decentralization | True P2P, no central control | Centralized servers | Decentralized volunteer relays |
| Speed | Good, AI-optimized routing | Varies by server load | Often slow |
| Anonymity | High, built-in encryption | High, but trust provider | Very high |
| Ease of Use | Learning curve for setup | Very easy | Complex for beginners |
| Censorship Resistance | High, dynamic routing | Varies, servers can be blocked | Very high |
What makes the IP2 network particularly appealing is its peer-to-peer architecture. Instead of routing through corporate servers or relying entirely on volunteers, it creates direct connections between users. This means better performance than Tor’s multi-hop routing, while offering greater resilience than VPN’s centralized model.
The trust model is also different. With VPNs, you’re trusting one company. With Tor, you’re trusting a global network of volunteers. The IP2 network distributes that trust across its decentralized network of nodes, reducing the risk of any single point compromising your privacy.
For a comprehensive breakdown of how these solutions compare in real-world scenarios, check out our detailed guide on IP2 Network vs. Other Network Solutions.
The choice ultimately depends on your specific needs and comfort level with technology. Just like choosing between a simple three-step skincare routine or a more comprehensive regimen, each approach has its place in maintaining your digital wellness.
How to Get Started with the ip2 network
Getting started with the IP2 network is like learning a new self-care routine; it becomes second nature once you understand the basics. A step-by-step approach will set you up for success.
The journey begins with installing an IP2-compatible router application on your device. The I2P Router GUI (Graphical User Interface) serves as your gateway to this more private internet experience. This software manages your connections and routes your traffic through the decentralized network.
Once your router is running, you can explore peer-to-peer (P2P) clients that work with the IP2 network. I2PSnark offers private file sharing, while Tribler provides decentralized file sharing across different platforms. These tools let you share content without compromising your privacy.
For those ready to dive deeper, setting up IP-over-P2P tunnels using tools like IPOP creates secure, VPN-like connections directly between devices. This advanced feature builds private bridges across the IP2 network, perfect for those needing extra security.
The final step involves configuring your applications to route traffic through your new IP2 network tunnel. Most web browsers and messaging apps allow proxy setting adjustments, which you can point to your local IP2 network router. Some users prefer dedicated browsers or extensions designed for this purpose.
Integrating the IP2 network into your routine can become as natural as your daily wellness practices. For detailed implementation guidance, our comprehensive guide on How to Use IP2 Network for Your Business provides step-by-step instructions.
Practical Applications and Use Cases
The IP2 network offers versatile applications that address various privacy and security needs, much like how different clean beauty products serve specific purposes.
Anonymous web browsing allows you to research sensitive topics privately, while secure file sharing and encrypted messaging keep your data and conversations confidential. The network also supports decentralized social media platforms and helps in bypassing geo-restrictions to access global content.
Beyond personal use, the IP2 network offers powerful enterprise solutions. Industries like finance, healthcare, and media benefit from secure transactions, reliable telemedicine, and improved streaming performance. Its ability to enable secure and efficient data transmission and strengthen cybersecurity makes it a valuable tool across diverse sectors, including government and defense.
Frequently Asked Questions about the IP2 Network
Exploring new technology can be overwhelming, especially when it concerns your digital privacy. We’ve gathered the most common questions about the IP2 network to help you feel more confident, just as you might ask a friend about switching to cleaner digital habits.
Is using the IP2 Network legal?
Yes, using the IP2 network itself is legal, as it’s simply a communication tool. However, what you do with the technology determines its legality. Using the network for illegal activities like copyright infringement or cybercrime remains illegal. The network is designed for privacy and security, not to shield unlawful behavior. Responsible use is key, so always follow local laws and use the tool ethically.
Does the IP2 Network require special hardware?
No, you don’t need any special equipment. The IP2 network is a software-based solution that works with your existing Windows, Mac, or Linux systems, and even some mobile devices. This ease of adoption means you can experiment with the network using the devices you already own without needing to buy new hardware.
What is the future outlook for the IP2 Network?
The future for the IP2 network is bright, especially as digital privacy concerns grow. Key developments include IoT integration for smart devices, compatibility with 5G and beyond, and potential quantum computing integration for future-proof encryption. The community is also focused on an improved user experience to make these privacy tools simpler for everyone. The IP2 network represents a shift toward a more user-controlled internet, putting control back in your hands – exactly where it belongs.
Conclusion
As we wrap up our journey through the IP2 network, it’s clear this technology is more than just another protocol. It’s about digital self-care – treating your online presence with the same thoughtfulness you give to choosing clean, nourishing skincare products.
It’s not just about technology; it’s about privacy as self-care and making conscious choices that protect your digital wellness.
Throughout this guide, we’ve seen how the IP2 network puts user empowerment at its core. Its decentralized architecture, built-in encryption, and censorship resistance are the building blocks of digital autonomy. The benefits all point to one central truth: you deserve control over your digital life.
Just as Beyond Beauty Lab believes in educating people about clean beauty, understanding technologies like the IP2 network is essential for holistic wellness in our connected world. Your digital footprint is part of your overall well-being. By choosing privacy-first technologies, you’re practicing a form of digital wellness that complements the physical and mental wellness you already prioritize.
Ready to take the next step in your digital wellness journey? The IP2 network offers a path toward a more secure, private, and resilient online experience. It’s time to treat your digital life with the same care you give every other aspect of your wellness routine.
Explore more on digital wellness and security and find how Beyond Beauty Lab’s educational mission extends beyond traditional beauty into the field of complete digital wellness.