Understanding 8tshare6a Software: What You Need to Know
8tshare6a software is not actually a legitimate software program – it’s a label used for pirated software bundles distributed through illegal file-sharing networks. Here’s what you need to know:
Quick Facts:
- What it is: A filename convention for cracked/pirated software packages
- Contents: Illegally modified versions of paid software like Adobe Creative Suite, Microsoft Office
- Sources: Warez forums, Reddit, Telegram channels, YouTube descriptions
- Legal status: Completely illegal – constitutes copyright infringement
- Safety: High risk of malware, viruses, ransomware, and data theft
If you’ve encountered references to “8tshare6a software” online, you’re likely looking at pirated software bundles that contain modified versions of popular programs. These aren’t official products from any legitimate company.
The term serves as an internal identifier used by people who distribute cracked software. These bundles often require you to disable your antivirus software during installation – a major red flag that should immediately raise concerns about your digital safety.
Real user experiences from our research reveal serious consequences: one Reddit user reported finding a hidden cryptominer that damaged their computer, while another experienced a trojan infection that compromised their banking information and required a complete system reinstall.
For those seeking digital wellness and clean technology habits – much like choosing clean beauty products – avoiding these risky downloads is essential for maintaining your cybersecurity health.

Related content about 8tshare6a software:
What is “8tshare6a Software” Really?
When you first come across the term “8tshare6a software,” it might sound like some innovative new app or productivity tool. Maybe something sleek and modern that helps with file sharing or creative work? Unfortunately, the reality is much less appealing – and far more dangerous for your digital wellness.
8tshare6a software isn’t actually a real software product at all. It’s simply a piracy label used to disguise bundles of cracked, unlawful copies of popular programs. Think of it like counterfeit beauty products sold under fake brand names – they might promise the same results as the real thing, but they come with serious hidden risks.
These software bundles typically contain modified versions of expensive programs from legitimate companies like Adobe and Microsoft. The modifications are designed to bypass licensing systems, essentially stealing these programs and redistributing them illegally.
You’ll find these packages circulating through shady file-sharing communities and warez forums – the digital equivalent of back-alley beauty product sales. Just as we’d never trust our skin to mysterious creams from questionable sources, we shouldn’t trust our computers to these risky downloads.
The appeal is obvious: why pay hundreds of dollars for professional software when you can get it “free”? But like those too-good-to-be-true beauty deals, the hidden costs can be devastating.
The Types of Programs Found in 8tshare6a Bundles
So what exactly lurks inside these suspicious software packages? Our research shows they’re typically stuffed with high-value commercial programs that have been illegally copied and modified.
Video Editing Tools are extremely popular in these bundles. You might find pirated versions of professional editing software that normally costs hundreds of dollars. These complex programs are particularly risky when cracked, as they often hide malware deep within their code.
Office Suites make up another huge category. Since almost everyone needs word processing and spreadsheet tools, these productivity programs are prime targets for pirates. The irony? Many people don’t realize there are excellent free alternatives available legally.
Photo Editing Software is also commonly bundled. Professional-grade photo editors with their expensive subscription fees become tempting targets. But downloading cracked versions is like using expired makeup – you never know what harmful surprises might be lurking inside.
PDF Utilities round out many packages, offering advanced document editing features without the legitimate licensing costs. Again, the “free” price tag masks serious security and legal risks.
Game Hacks and cheating tools sometimes appear in these bundles too, targeting gamers who want unfair advantages. These modifications are particularly notorious for containing malicious code.
The pattern is clear: if a program normally costs money, there’s probably a pirated version floating around in these illegal bundles.
Why This Name? The Origin of the Term
The weird name “8tshare6a software” probably seems random – and that’s exactly the point. Unlike real software with memorable brand names, this is just an internal identifier used by people who distribute cracked programs.
Think of it as a secret code word used in underground communities. These cryptic names help pirates organize their illegal activities while staying under the radar. The term likely originated from filename conventions used in online forums where this stuff gets shared.
You’ll encounter these mysterious identifiers on platforms like Reddit in certain piracy-focused communities, or in private Telegram channels where people trade illegal software. Sometimes they even show up in YouTube video descriptions disguised as “helpful” software tutorials.
The lack of official branding is actually a huge red flag. Legitimate software companies want you to know their names – they invest millions in marketing and brand recognition. When software comes with vague, random identifiers instead of clear company backing, that’s your cue to run the other direction.
Just like how sketchy beauty products often have confusing names and unclear origins, 8tshare6a software and similar terms are designed to obscure rather than inform. It’s intentionally murky because transparency would expose the illegal activity behind it.
This naming confusion serves the pirates well, but it should serve as a warning to the rest of us. Clear, honest branding is a sign of legitimate business – whether we’re talking about skincare products or software programs.
The Hidden Dangers: Why 8tshare6a Software Threatens Your Digital Wellness
Just like we carefully read ingredient labels on our skincare products and choose clean beauty options for our physical wellness, we need to be equally mindful about our digital wellness. Think of downloading 8tshare6a software as putting mystery ingredients on your face – you simply don’t know what harmful substances might be lurking inside.
The truth is, using pirated software creates serious threats to your data privacy and system integrity. When you download these unauthorized programs, you’re essentially inviting unknown guests into your digital home without any background checks. Unlike legitimate software from trusted companies, these pirated versions bypass all the normal security measures that keep your computer safe.
The Software Alliance (BSA) consistently warns users about the severe risks that come with software piracy. Their research shows that pirated software often contains malicious code that can steal your personal information or damage your computer. Meanwhile, organizations like Europol work around the clock to combat the cybercrime networks that distribute these dangerous programs.
The scary part? Most people who download 8tshare6a software have no idea they’re putting themselves at risk. They think they’re just getting free software, but they’re actually opening the door to serious digital threats.
Malware, Ransomware, and Viruses
Here’s where things get really frightening. When you install 8tshare6a software, you’re not just getting the program you wanted – you’re often getting a whole package of malicious software that can destroy your digital life.
Trojans are particularly sneaky. They hide inside what looks like normal software, but once installed, they create secret backdoors that let hackers control your computer remotely. Imagine someone having the keys to your house while you’re sleeping – that’s essentially what a Trojan does to your digital space.
Ransomware might be even worse. This nasty software can lock up all your precious photos, important work documents, and personal files. Then it displays a scary message demanding you pay hundreds or thousands of dollars to get your files back. Picture waking up one morning to find all your digital memories held hostage – it’s absolutely devastating.
Spyware and keyloggers work more quietly but are just as dangerous. These programs secretly watch everything you do on your computer. They record your passwords, track your online banking, and steal your personal information. Every email you write, every website you visit, every password you type – it’s all being recorded and sent to criminals.
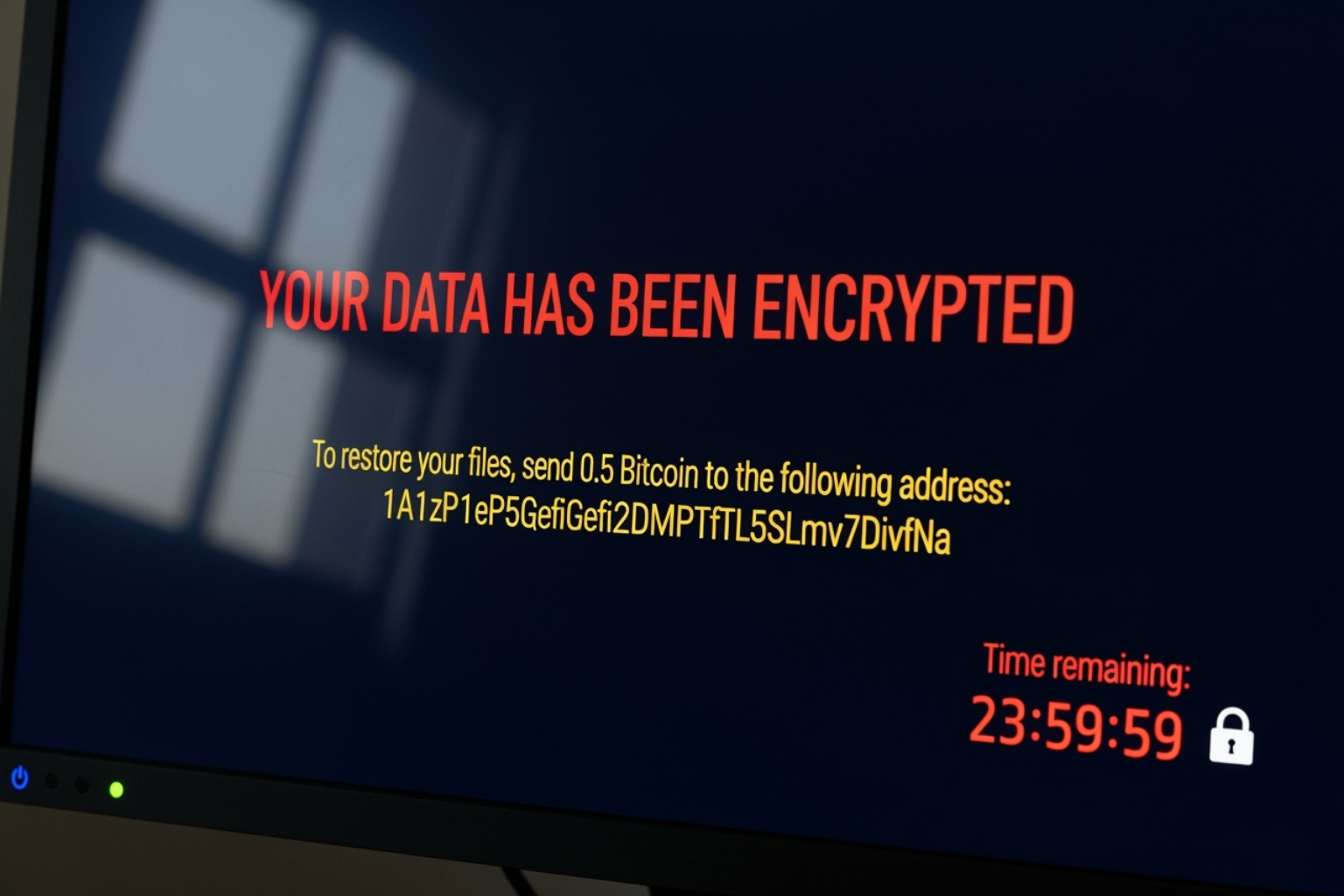
Real users have shared heartbreaking stories about these infections. One person downloaded what they thought was Adobe After Effects from an 8tshare6a bundle, only to find a hidden program was secretly mining cryptocurrency on their computer. Their computer overheated so badly they had to replace the entire hard drive.
Another user’s story is even more chilling. After downloading 8tshare6a software, Windows Defender detected a Trojan, but by then it was too late. Hackers had already gained access to their online banking. They lost money, had to change all their passwords, and ultimately had to completely wipe their computer and start over. The financial loss and stress lasted for months.
Legal Repercussions and Ethical Concerns
Beyond the terrifying security risks, there’s another serious problem: using 8tshare6a software is completely illegal. This isn’t a gray area or a minor rule – it’s full-blown copyright infringement that can land you in serious legal trouble.
The legal penalties can be harsh. People have faced thousands of dollars in fines for using pirated software. Companies like The Software Alliance (BSA) actively hunt down software pirates and pursue legal action. What seemed like saving money on software can quickly turn into a legal nightmare that costs far more than just buying the legitimate version would have.
There are important ethical concerns too. When you use pirated software, you’re essentially stealing from the developers who spent years creating these programs. These are real people with families who depend on software sales to make a living. By choosing pirated versions, you’re hurting the very people who create the digital tools we all rely on.
Perhaps most frustrating of all, pirated software comes with absolutely no technical support. When something goes wrong – and it often does – you’re completely on your own. There are no updates to fix bugs or security holes, no customer service to call, and no guarantee the software will work with future operating system updates. You’re trading short-term savings for long-term headaches and vulnerability.
The lack of updates is particularly dangerous because it means your pirated software becomes more vulnerable to attacks over time. It’s like using expired sunscreen – it might seem fine at first, but it won’t protect you when you really need it.
How to Practice Safe and “Clean” Digital Habits
Think of your digital life the same way you approach your skincare routine – with intention, care, and quality products. Just as Beyond Beauty Lab champions clean beauty choices for your physical wellness, we believe in cultivating clean digital habits for your online health. When it comes to protecting yourself from threats like 8tshare6a software, being proactive is your best defense.
Your computer needs protection just like your skin needs sunscreen. Antivirus software acts as your digital SPF, creating a barrier against harmful elements trying to penetrate your system. A properly configured firewall works alongside it, monitoring what comes in and goes out of your network. These aren’t optional extras – they’re essential daily protection.
The key is building security into your routine before you need it. This means always verifying sources before downloading anything, scanning files with your antivirus before opening them, and actually reading installation prompts instead of clicking through blindly. We know it’s tempting to rush, but taking these extra moments can save you hours of headaches later.
For those curious about how digital security intersects with the broader online economy, our comprehensive guide on FintechZoom: Your Ultimate Guide to the Digital Economy explores how to steer secure digital environments across various platforms. Understanding these best practices for safety and security creates a foundation for all your online activities.
Identifying and Avoiding Unsafe Sources
Learning to spot suspicious software sources is like developing an eye for questionable beauty products – once you know what to look for, the red flags become obvious. The internet is full of sites promising “free” versions of expensive software, often using labels like 8tshare6a software to disguise their true nature.
Unofficial links are everywhere – shared in forums, social media comments, or video descriptions promising full versions of premium programs. These are almost always traps. Peer-to-peer networks might seem harmless for sharing files, but they’re also prime hunting grounds for malware distributors. And those shady advertisements with flashing “Download Now!” buttons? They’re designed to catch you in a moment of impatience.

So where can you safely find software? Official developer websites are always your safest bet – if a program doesn’t have a legitimate website, that’s a major warning sign. Trusted platforms like GitHub host many open-source projects, while Softpedia vets software for safety before listing it.
The golden rule is simple: if a deal seems too good to be true, it probably is. No legitimate company gives away their premium software through sketchy download sites or anonymous file-sharing networks.
Advanced Protection: Using a Sandbox
For tech-savvy users who absolutely must test questionable software (though we strongly advise against anything labeled 8tshare6a software), a sandbox environment offers an extra layer of protection. Think of it as a digital quarantine room where suspicious programs can’t escape to infect your main system.
A virtual machine creates this isolated environment – essentially a computer within your computer. Tools like VirtualBox let you set up a completely separate operating system that runs independently from your main one. If malware strikes the virtual machine, you can simply delete it without any damage to your actual computer.
The process is straightforward: create a fresh virtual machine, test any suspicious software there first, and contain any threats within that isolated space. It’s like having a separate testing lab where you can safely examine unknown substances without risking contamination of your main workspace.
Before running anything, even in a sandbox, consider using online scanning services that check files against multiple antivirus engines. This gives you an early warning if a file is known to be dangerous. These advanced protection methods represent the pinnacle of clean digital practices – taking every precaution to keep your digital wellness intact.
Legitimate and Safe Alternatives to Pirated Software
Think of choosing software like choosing skincare products – you want something that’s safe, effective, and ethically sourced. We’ve talked about why 8tshare6a software is like using a mystery cream with unknown ingredients that could harm your skin. But what if you genuinely need powerful tools for creative work or productivity, and your budget feels tighter than your favorite jeans after the holidays?
Here’s the beautiful truth: the digital world is overflowing with legitimate, safe, and often completely free alternatives. These aren’t knockoffs or compromises – they’re often created by passionate communities who believe great tools should be accessible to everyone.
Open-source software has revolutionized how we think about digital tools. These programs are developed by communities of volunteers and professionals who share their code openly. It’s like having a recipe that everyone can see, improve, and verify is safe. Freemium models offer another path – you get solid basic features for free, with the option to upgrade if you need more advanced capabilities.
When you choose these legitimate options, you’re not just protecting your computer from malware and legal headaches. You’re supporting ethical development and joining a community that believes in sharing knowledge and tools. It’s the digital equivalent of choosing clean beauty products – better for you and better for the world.
For those interested in understanding how security plays a role in the broader digital economy, our guide on FintechZoom: Crypto Ultimate Guide offers fascinating insights into navigating secure online environments.

[TABLE] comparing Pirated Software vs. Legitimate Free Alternatives
Let’s break down the real difference between the hidden costs of 8tshare6a software and the genuine value of legitimate alternatives. Sometimes seeing the facts side by side makes everything crystal clear:
| Feature | Pirated Software (e.g., “8tshare6a”) | Legitimate Alternatives (e.g., GIMP, LibreOffice) |
|---|---|---|
| Cost | “Free” (with hidden costs of malware, data loss, legal fines) | Free (or freemium with optional paid upgrades) |
| Security | High Risk (Malware, Viruses, Spyware, Ransomware, System Instability, Data Theft) | Safe and Secure (regularly scanned, community-vetted, official updates) |
| Legality | Illegal (Copyright Infringement) | Legal (Licensed under open-source or proprietary freemium terms) |
| Updates | None (or unofficial, potentially dangerous “updates”) | Regular Updates & Patches (for security, features, and compatibility) |
| Support | None (No official documentation, community, or developer support) | Community & Developer Support (forums, documentation, bug tracking) |
| Features | Often full functionality, but may be unstable or compromised | Robust functionality, continuously improving, transparent development |
| Ethical Impact | Harms developers, contributes to illegal economy | Supports open-source community, ethical development |
The “free” aspect of pirated software is like those too-good-to-be-true beauty deals that end up causing skin irritation. The real cost comes later, and it’s usually much higher than you’d expect.
Free Tools for Your Creative and Productivity Needs
We believe everyone deserves access to powerful digital tools without having to play digital Russian roulette. Here are some fantastic, legitimate alternatives that can help you achieve your creative and productivity goals safely.
For photo editing, instead of risking a pirated version of expensive software, try GIMP. This powerhouse is completely free and open-source, handling most professional image editing tasks with ease. The community around GIMP is incredibly supportive, with countless tutorials and resources available.
When it comes to video editing, DaVinci Resolve will absolutely blow your mind. This professional-grade video editor offers a surprisingly robust free version that rivals many paid applications. It includes advanced color correction, editing, and audio post-production tools that Hollywood studios actually use.
Need an office suite? LibreOffice is your new best friend. This comprehensive suite includes everything you need – word processing, spreadsheets, presentations, and more. It plays nicely with other office file formats, so you won’t have compatibility headaches.
For PDF editing tasks like merging, splitting, and converting documents, PDF24 Creator offers an impressive range of functionalities that often require paid software elsewhere.
These tools aren’t consolation prizes – they’re legitimate, powerful alternatives that millions of users rely on daily. By choosing them, you’re joining a community that values security, ethics, and shared knowledge. Plus, you’ll sleep better knowing your computer isn’t harboring any digital nasties from sketchy downloads.
Frequently Asked Questions about Unverified Software
When it comes to navigating the tricky waters of software downloads, we understand that questions naturally arise. The world of digital tools can feel overwhelming, especially when faced with tempting “free” options like 8tshare6a software. Just as you might ask your dermatologist about a new skincare ingredient, it’s perfectly normal to seek clarity about software safety. Let’s address the most common concerns we hear from our community.
Is 8tshare6a software legal to use?
The short answer is no – and there’s really no wiggle room here. Using 8tshare6a software falls squarely into the category of copyright infringement, which is illegal in virtually every country around the world. Think of it like using counterfeit beauty products – they might look similar to the real thing, but they’re unauthorized copies that violate intellectual property laws.
These pirated software bundles represent illegal distribution of commercial applications that developers have invested time, money, and creativity into creating. The legal penalties can be surprisingly severe, ranging from hefty fines to more serious legal consequences. It’s simply not worth the risk when there are so many legitimate alternatives available.
Is it ever safe to download 8tshare6a software?
Unfortunately, no – there’s no such thing as “safe” pirated software. This is one of those situations where the inherent risks make any potential benefits completely meaningless. Every download of 8tshare6a software comes with a cocktail of potential threats: malware, viruses, ransomware, spyware, and keyloggers are common companions to these illegal bundles.
The installation process itself is a red flag parade. Most pirated software requires you to disable your antivirus protection during installation – imagine being asked to remove your sunscreen before walking into harsh sunlight! There’s no guaranteed method to verify the safety of these files, and the potential for data theft, system damage, and privacy breaches far outweighs any perceived savings.
What should I do if I already installed software from an untrusted source?
If you’ve already installed 8tshare6a software or any other questionable program, don’t panic – but do act quickly. Think of this as emergency first aid for your digital life.
Disconnect from the internet immediately by unplugging your ethernet cable or turning off Wi-Fi. This prevents malware from communicating with external servers or spreading to other devices on your network.
Next, run a comprehensive antivirus scan using reputable, up-to-date security software. Let it quarantine or remove any threats it finds. Consider using a second scanner from a different vendor for extra thoroughness.
Backup your important data if your system is still functioning, but be cautious. If you suspect ransomware or rootkits, you might be backing up compromised files. A clean backup from before the infection is ideal.
Change all your important passwords from a different, clean device. Assume that any passwords stored on or accessed from the compromised computer have been stolen. Update your email, banking, social media, and other critical account passwords, and enable two-factor authentication wherever possible.
Finally, consider a complete operating system reinstallation. While this sounds drastic, it’s often the most effective way to ensure all malicious software is completely removed. Back up essential files (after thorough scanning), format your hard drive, and reinstall your operating system from a legitimate source. This gives you a fresh, clean digital slate – much like starting a new skincare routine with verified, safe products.
Taking swift action protects your valuable data and helps restore your digital peace of mind. Your digital wellness is just as important as your physical wellness.
Conclusion
As we wrap up our deep dive into 8tshare6a software and digital safety, it’s clear that protecting our digital wellness is just as important as caring for our physical health. Think of it this way: you wouldn’t put mystery ingredients on your skin without knowing what they are, so why would you install unknown software on your computer?
The temptation of “free” premium software can be strong, especially when budgets are tight. But as we’ve seen throughout this guide, 8tshare6a software and similar pirated programs come with hidden costs that far outweigh any perceived savings. From devastating malware infections to legal troubles, the risks simply aren’t worth it.
The beauty of making informed choices extends beyond skincare and wellness products – it applies to every aspect of our digital lives. When we choose legitimate software alternatives like GIMP, LibreOffice, or DaVinci Resolve, we’re not just protecting our computers. We’re supporting ethical development, ensuring regular security updates, and gaining access to genuine community support.
Your digital wellness matters. Just as Beyond Beauty Lab believes in clean, safe beauty practices, we encourage you to accept clean digital habits. This means downloading software only from trusted sources, keeping your antivirus protection active, and never disabling security features for the sake of a “free” download.
The peace of mind that comes from knowing your system is secure and your data is protected is invaluable. You can focus on what matters most – whether that’s creating beautiful content, managing your daily tasks, or exploring new digital possibilities – without constantly worrying about cyber threats lurking in the background.
Cybersecurity truly is a form of self-care. By making conscious, informed decisions about the software we use, we’re investing in our long-term digital health and protecting everything we’ve worked hard to build online.
There’s a world of legitimate, powerful, and often free software alternatives waiting for you. The choice between risky pirated software and safe alternatives is really a choice between fear and confidence, uncertainty and peace of mind.
Explore more on how to improve your overall wellness and continue building healthy habits that support both your physical and digital well-being. After all, true beauty and wellness encompass every aspect of our modern lives.